Third-party risk management (TPRM) is a non-negotiable fact of life for any organization that outsources its activities. Understanding the third-party risk management lifecycle can ensure your TPRM operates at maximum effectiveness.
What is the Third Party Risk Management Lifecycle?
Third-party risk management is the process of managing the threats that suppliers and vendors can introduce to your organization.
Like many processes, TPRM is circular, one that needs to be revisited regularly to ensure you are minimizing the risks of your third-party relationships. It has a lifecycle, and understanding this lifecycle — and ensuring you follow all the stages — can be an essential step in your TPRM program.
There are plenty of reasons why third-party risk management isn’t a one-time exercise. Firstly, external factors may impact your third-party relationships and the ability of suppliers to deliver. A crisis like the war in Ukraine has the potential to up-end supply chains overnight.
A vendor or supplier’s circumstances may change; they may suffer a risk event that changes the risk they pose to your business. Natural disasters or geopolitical events can disrupt a third party’s operations.
Even without external influences, there are stages in the lifecycle of a third-party relationship that need to be assessed through the lens of risk.
As a result, it’s important to understand and regularly revisit all the stages in the third-party risk management lifecycle.
The Stages of the Third-party Risk Management Lifecycle
What are the stages of the third-party risk management lifecycle?
Look up a dozen articles on this topic and you will get a dozen “definitive” lists covering the stages in the TPRM lifecycle. These can range in detail from three stages upwards.
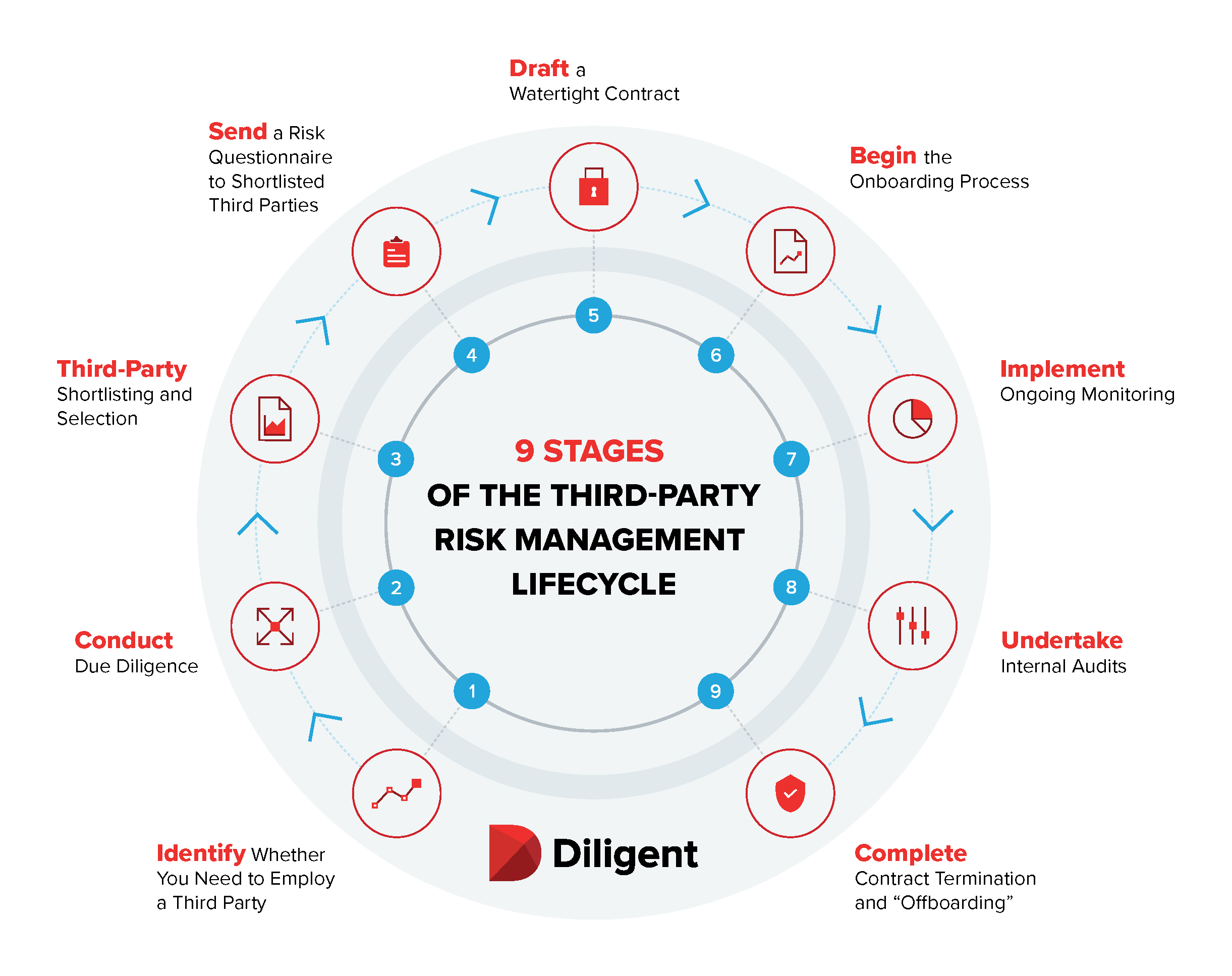
We have identified nine stages in the third-party risk management lifecycle — here they are.
1. Identify Whether You Need to Employ a Third Party
The first question to ask is whether you need a third party at all. Is the task in question one that only an external vendor can do? There are times when the answer is an unequivocal “yes.” In some cases, it is a specialist role that no one in your organization can undertake, or employing a third party will bring expertise and efficiency not available in-house.
Consider creating a checklist of criteria that must be met before hiring a third party; there may be good reasons, but ensuring they outweigh the risks is worthwhile.
2. Conduct Due Diligence
Once you’ve ascertained that a third party is needed, do your due diligence. This may involve several internal teams; risk isn’t just about cybersecurity. Does the provider have the size and resources to deliver to your deadlines? Can their operations meet your specifications? Do they have the same standards around business integrity and ESG as you do?
Answering these questions may require the involvement of your engineering and procurement teams, as well as IT and compliance.
Consider too the inherent risk posed by different vendors; a catering supplier to run your canteen will have a different risk profile than an IT vendor hosting your data. As well as the service provided, risk profiles may vary depending on a third party’s location, history, compliance record and so on.
Are the vendors you’re considering certified to any external frameworks? For instance, assessing whether your preferred third party is NIST 800-53 compliant gives you a sense of how seriously they take their cybersecurity.
Often these various elements of due diligence are carried out in isolation and inconsistently. You may want to explore ways technology can help create a more consistent due diligence process.
3. Third-Party Shortlisting and Selection
When presenting a shortlist of third-party suppliers, vendor risk management should be a key aspect.
Be specific and transparent about the reasons each business has been shortlisted and any risk factors that those making the selection should know, giving the panel a full and fair view of the risks posed by the appointment.
4. Send a Risk Questionnaire to Shortlisted Third Parties
Issue a questionnaire to all potential third-party providers. The questionnaire will cover issues like:
- Company ownership
- Registered office location and location of operations
- The financial health of the business; credit history, and any issues to be aware of
- Compliance processes, and in particular, any noteworthy compliance breaches
- IT policies, practices and safeguards
You won’t be able to use a “one size” questionnaire for all third parties or in all circumstances. Tailoring your TPRM questionnaire is essential to get the answers you need to take an informed view on supplier selection.
And don’t just ask about risks and breaches, but also about remediation. Many companies can fall prey to threat actors; their actions and measures to prevent future occurrences can be equally important when assessing their risk profile.
5. Draft a Watertight Contract
Once your due diligence and questionnaire have helped you to choose the right third party, you move to the contract phase. Drawing up a contract that supports your vendor risk management strategy is a vital step in the third-party risk management lifecycle.
Ensure the contract meets best practice standards for your industry and enables you to respond robustly to any issues around service levels, compliance breaches or other risk factors.
6. Begin the Onboarding Process
Onboarding doesn’t just mean introducing a supplier to your business and your way of working. It can involve giving them access to your systems and operations.
From a third-party risk management perspective, it requires uploading information on the supplier to your systems so you have complete visibility of their involvement in your organization.
Onboarding should come with a formalized approval process. All contractual terms and other processes agreed with the supplier, such as data access and processing, should be documented. Compliance should be a central tenet of any onboarding process. Deadlines for getting suppliers fully integrated into your organization should be realistic.
7. Implement Ongoing Monitoring
The third-party risk management lifecycle demands that monitoring doesn’t stop after onboarding a vendor. As your relationship progresses, it may change, with providers given more access to corporate confidential information than initially envisaged. Overseeing third-party risk should be a long-term focus.
On an ongoing basis, you should monitor factors including:
- Compliance and compliance reporting
- The controls the third party has in place to prevent breaches
- Performance requirements and SLAs
- The key performance indicators (KPIs) and key risk indicators (KRIs) the vendor uses to monitor their own performance
8. Undertake Internal Audits
Alongside your own ongoing monitoring, your internal audit team is an invaluable line of defense against third-party risk.
Internal audit brings a degree of impartiality to third-party risk management, so involving your audit team can play a crucial role in the third-party risk management lifecycle.
In addition to an extra layer of rigor, your internal audit team will likely have existing methods for assessing and reporting on third parties, bringing consistency and, potentially, a degree of automation that can enhance efficiency and effectiveness in third-party risk management.
9. Contract Termination and “Offboarding”
Contracts come to a natural end; occasionally, they're terminated before that point. Whatever the reason you need to offboard a supplier, there are specific steps you should go through to minimize risk.
Revoke access to your systems, premises and data. Document the reasons for the contract termination, whether in the plan or not. If the onboarding process was documented correctly, you have a head start, as you will have evidenced things like systems access and the members of a supplier organization who have right of entry to your offices. Documented SLAs and KPIs make it easier to identify if all contractual terms have been met.
Implement Best Practice at All Stages of the Third-party Risk Management Lifecycle
The TPRM lifecycle should form the basis of your approach to vendor risk management. Understanding and working through the vendor management lifecycle stages will bring structure and rigor to your third-party risk management.
Find out how to make your approach to the third-party risk management lifecycle more consistent, straightforward and robust by downloading Technology and Risk Management: A Checklist for Successfully Managing IT Risk & Third-Party Risk from Diligent.