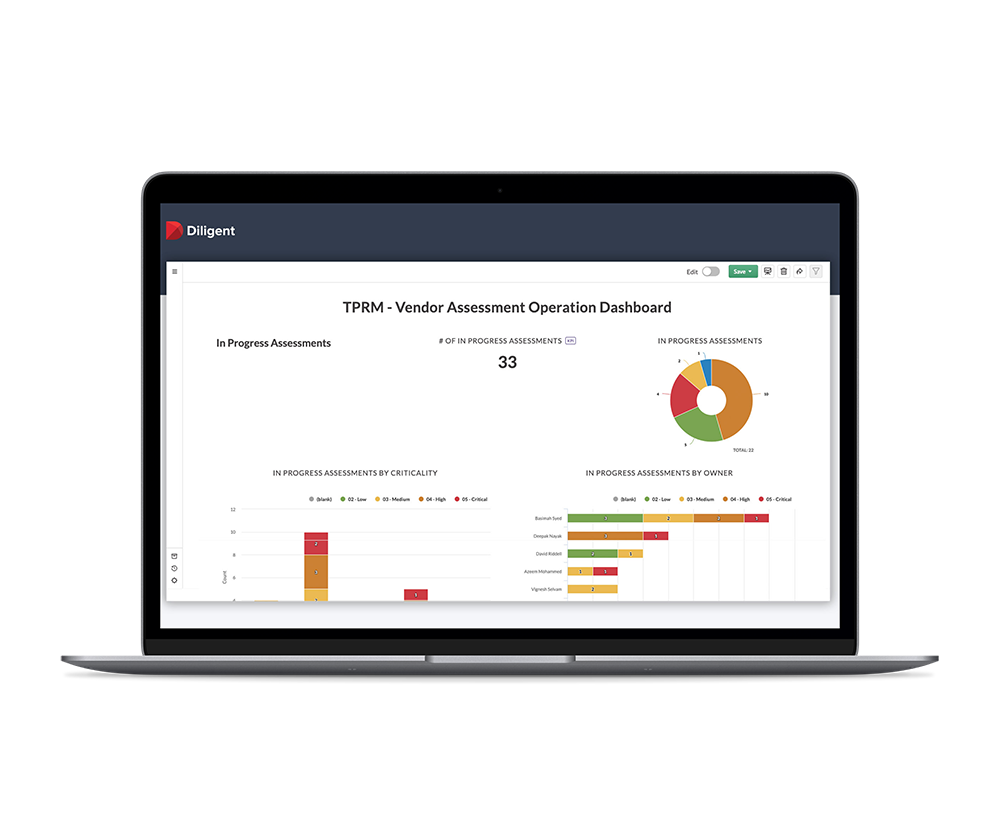
Streamline Vendor Onboarding & Classification
- Send assessment surveys to new and existing vendors, delivering a full vendor profile for review
- Select viable third-party vendors and prioritize risk remediation
- Manage contracts with a flexible workflow and sign off process
- Centralize the collation and storage of all completed surveys and risk assessments for your audit trail
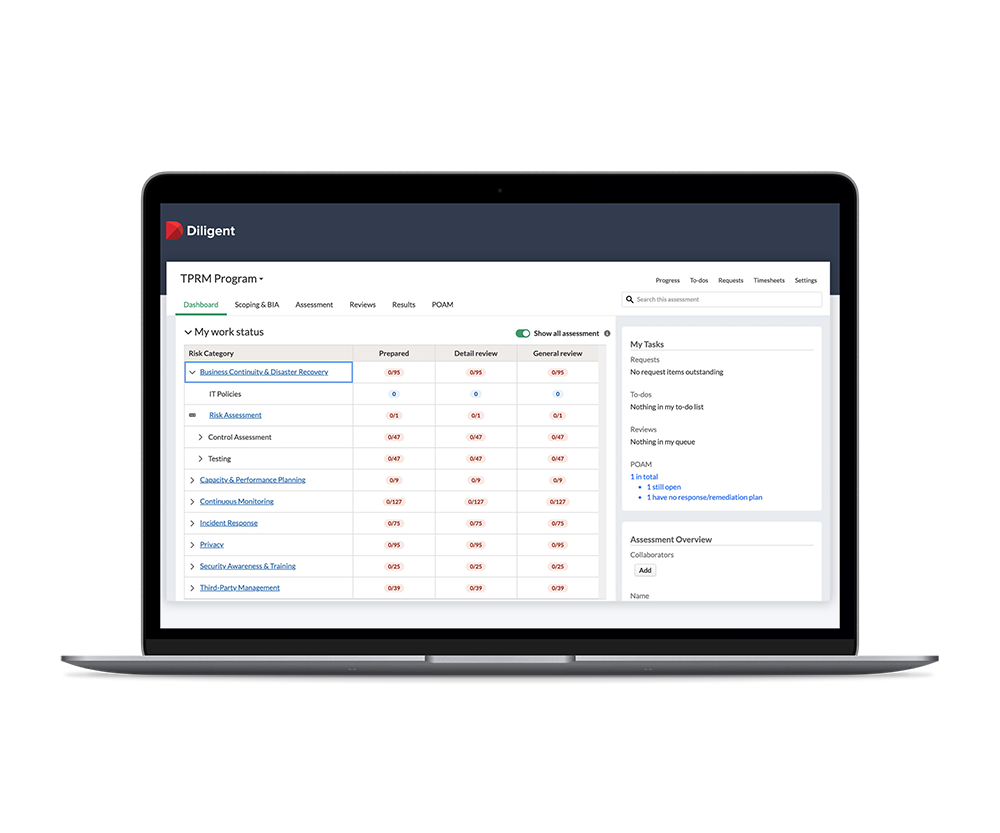
Centralize Third-Party Vendor Management
- Track essential third-party data in a central location, including audit findings from site visits, real-time financial data feeds and service level agreements
- Automate collaboration across all departments, connecting data from existing tools to develop enhanced insights
- Use built-in risk scores and integrate independent security ratings to categorize vendors and monitor risk
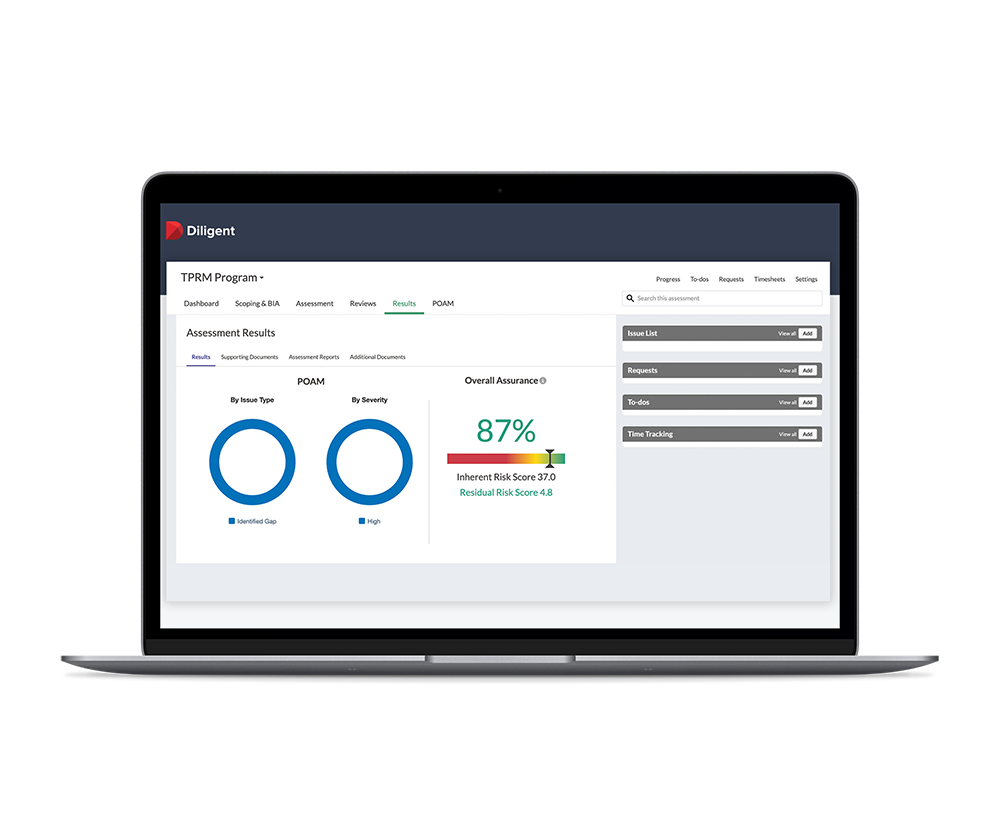
Make Informed, Data Driven Decisions
- Compare risks presented by all vendors in an easy-to-use matrix
- Prioritize remediation of areas of concern and reduce the potential of a costly security breach or noncompliance penalties
- Use customizable reporting to provide leadership teams with the insights they need to make critical business decisions
Build Resilience With Scalable Third-Party Risk Management
Talk to one of our experts and find out how our proactive approach to risk management can work for you
Related Insights & Resources

ARTICLE
Here, we discuss how a robust third-party risk management policy helps to ensure your organization is less susceptible to cyber-attacks and breaches.

BLOG
When building the foundations of a formal third-party risk management program, it’s critical to factor in the needs of your clients — both internal and external. Here’s how you can deliver against their expectations.

ARTICLE
Select third-party risk management metrics the board can appreciate. Here, we provide best practices for choosing the right metrics to build a robust TPRM program.



