Meet Federal Requirements While Saving Time and Resources
Centralize your IT compliance program into a single system that can help you attain necessary authorizations for federal contracts. Streamline your compliance efforts to save your organization time and money through automation and continuous monitoring, all from a single FedRAMP and DOD IL5-authorized platform.
Manage Your Security Certifications
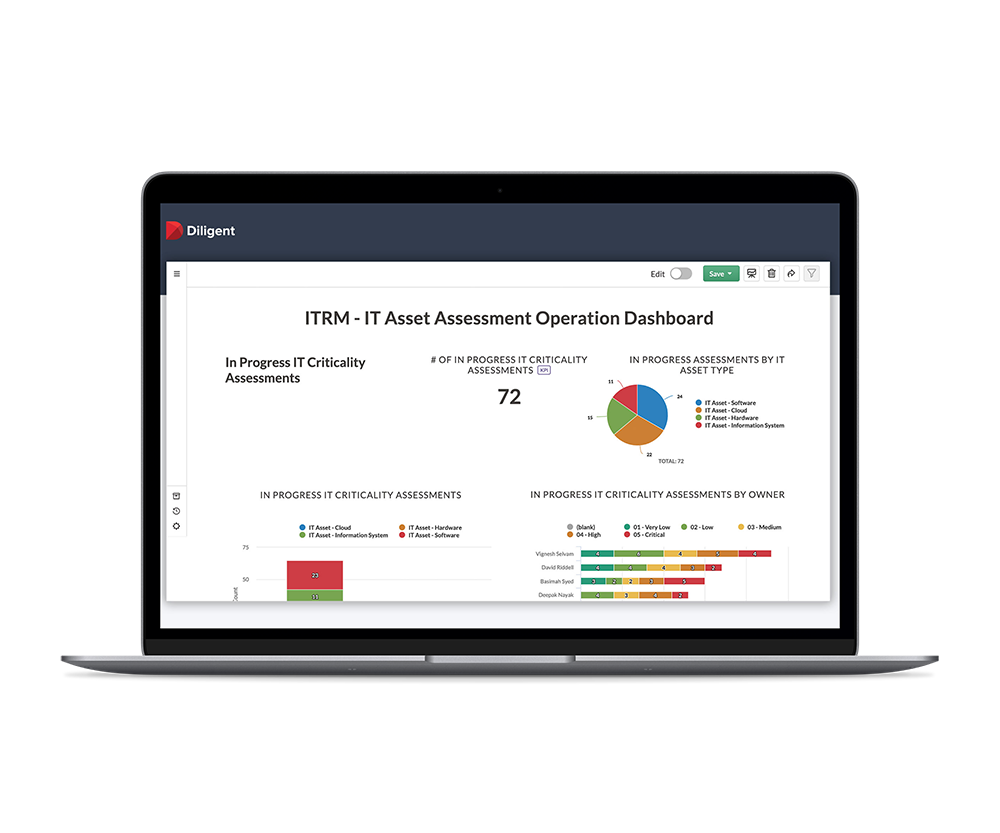
With out-of-the-box capabilities, we enable IT teams to manage and monitor compliance for 75+ standards, guidelines, frameworks, and regulations.
Ensure IT Compliance With U.S. Federal Security Requirements
Build your IT compliance program in a FedRAMP and DOD IL5-authorized cloud environment so you can maintain essential federal government contracts and avoid the risk of revenue loss.
- Deliver a robust IT compliance program that meets the frameworks required by U.S. government agencies, including FedRAMP, CMMC, NIST 800-171, FISMA, NIST 800-53 and more
- Scale up to cover additional frameworks that open new revenue opportunities with the U.S. federal government
- Showcase a consolidated view of your IT compliance program so you can maintain security authorizations required for federal contracts
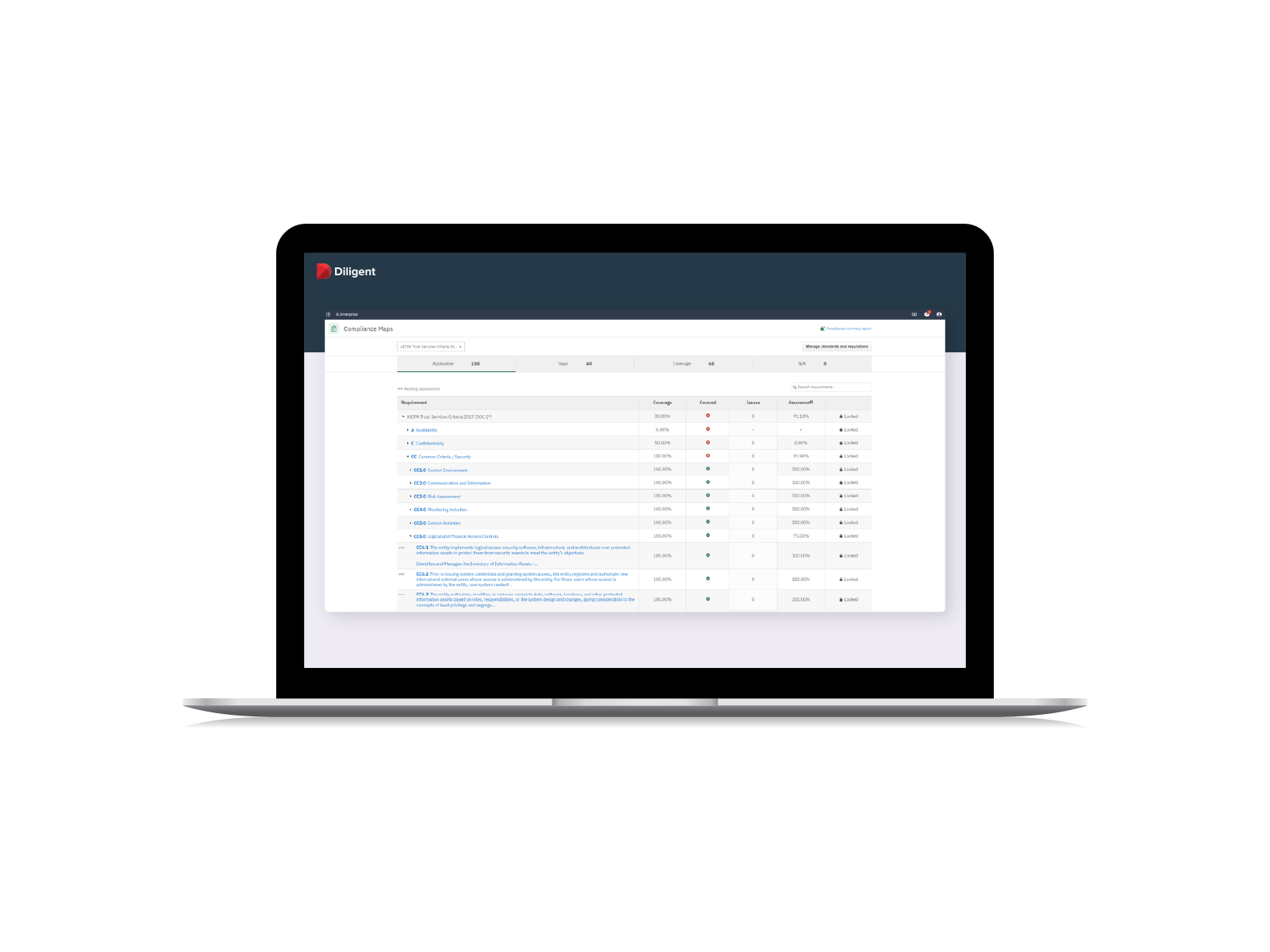
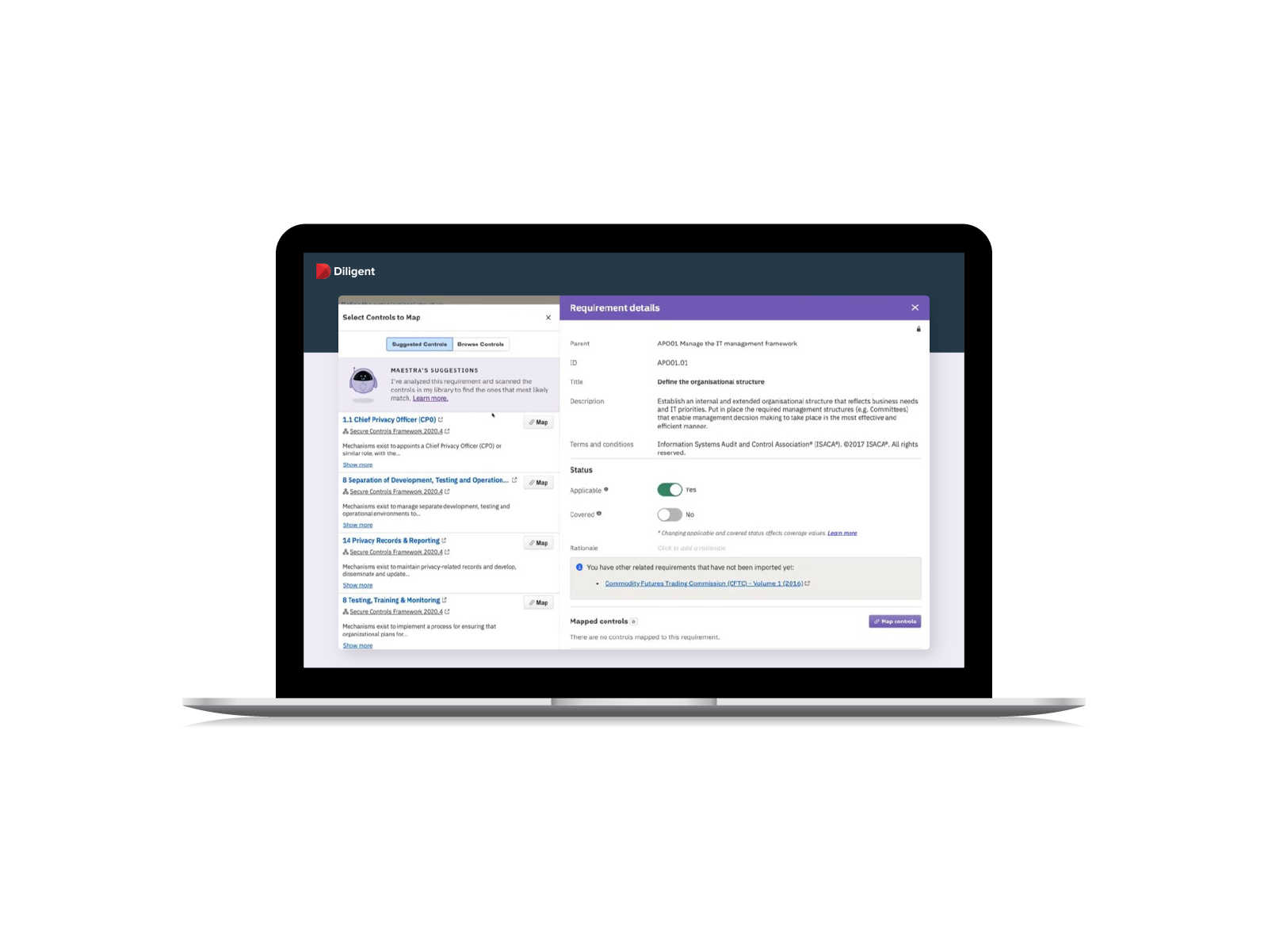
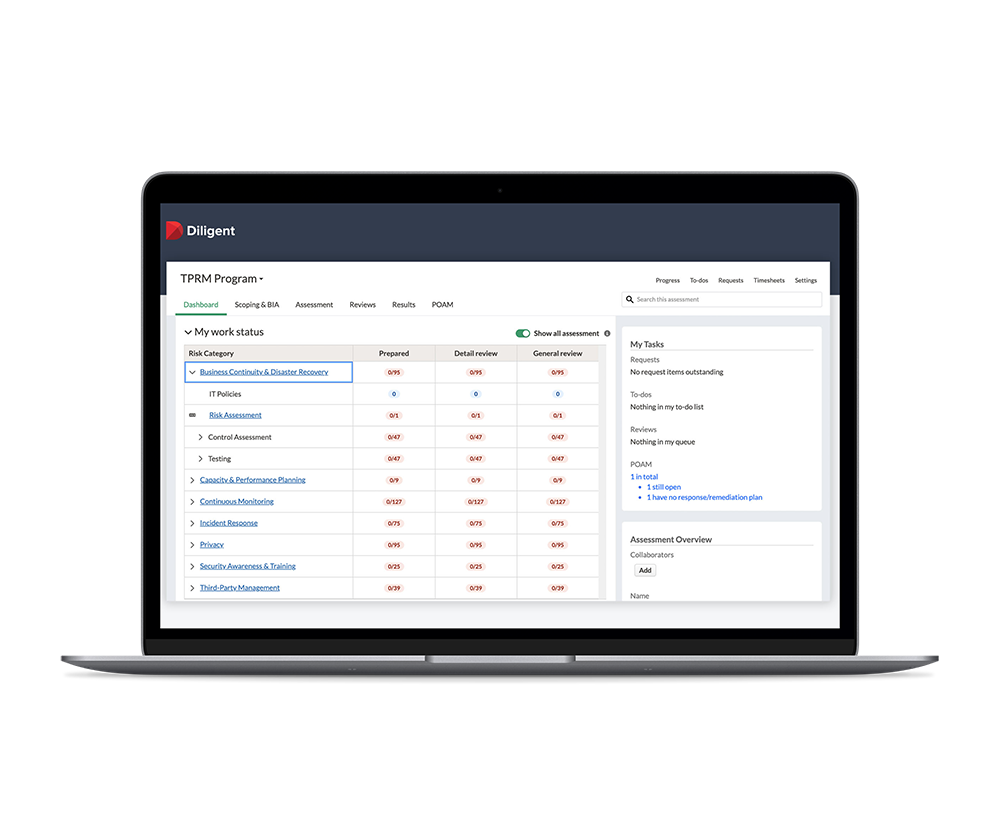
Centralize Your IT Compliance Into a Single System
Achieve greater efficiency, scalability and visibility by automating your security compliance program from a centralized, single source of truth.
- Complete initial authorization, certification and auditing across multiple frameworks and environments
- Automate the delegation of evidence collection to control owners using scheduled surveys
- Prepare for committee meetings with ready-to-use reports that deliver an aggregated view of authorization and compliance efforts to reassure the board and C-suite
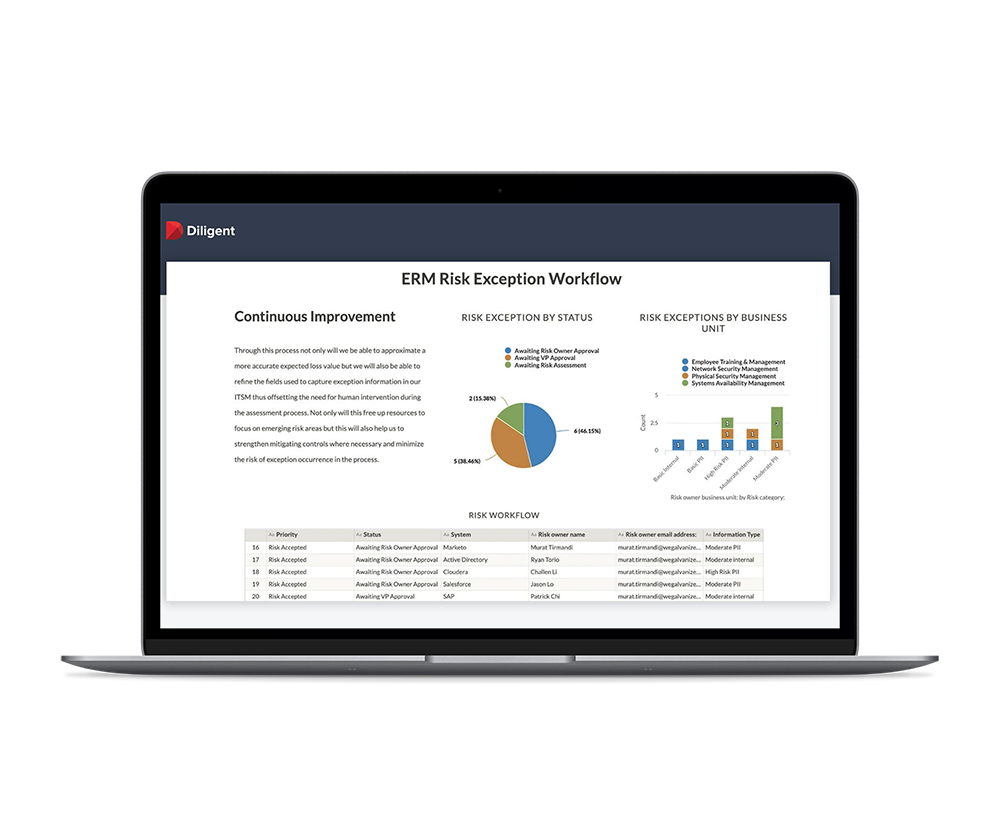
Save Critical Time With Automation and Continuous Monitoring
Build a more efficient IT compliance program that gives time back to your team for strategic initiatives.
- Use out-of-the box toolkits with pre-configured regulations and control baselines that help you get started quickly
- Build controls once and leverage an AI engine to accelerate mapping to multiple requirements, saving you time by building a common controls framework
- Boost employee morale by replacing repetitive, manual efforts with automated surveys, remediation and centralized evidence collection for audit-readiness
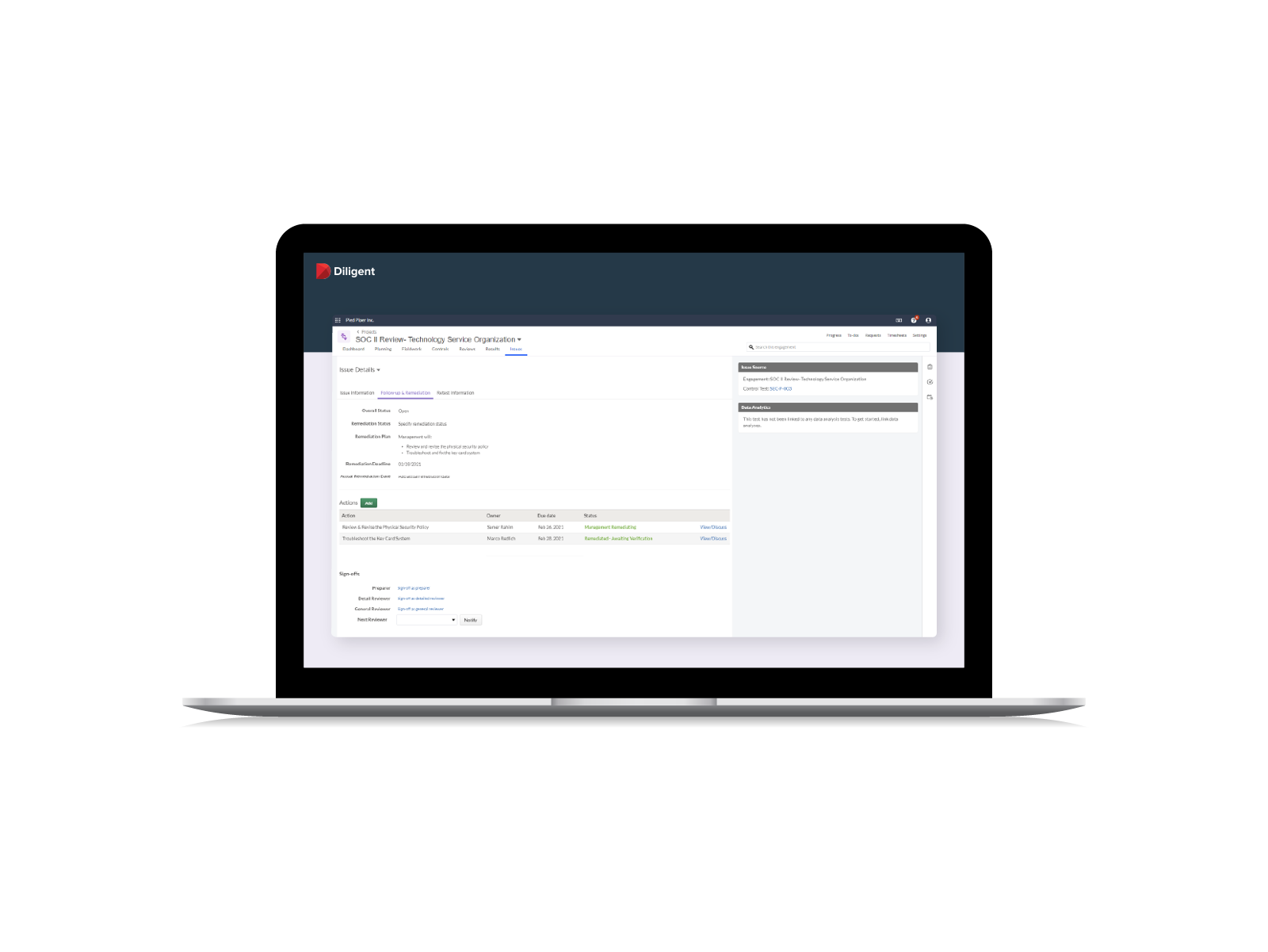
- Continuously monitor controls to quickly identify and remediate deviations, reducing risks and demonstrating the organization’s commitment to information security
Related Insights and Resources






RESPONSIVE
24/7/365
Award-Winning-Support
1,500+
Dedicated Employees
TRUSTED
25,000+
Customers
1,000,000
Users
IMPACTFUL
700,000+
Board Members & Leaders
130
Countries
Speak with an expert advisor to arrange a custom demo
See how can we help you drive success with a demo customized to your workflow and business objectives
“Not only is the training great, but the tool’s capabilities are fantastic and will lead to several process efficiencies and opportunities.”
Manager, IT Service Management & Compliance