Security Controls Mission Statement
Confidentiality and integrity of customer data is our most important mission. We make all commercially and professionally reasonable efforts to maintain the highest levels of each, as customers would expect from us and themselves. We regularly assess risk, monitor our controls, evaluate potential threats, and use this information to update our controls framework from policies and procedures to encryption protocols.
Our Commitment
We are committed to providing a robust and secure service that protects our customers’ data. We provide our service to customers and we also use it ourselves— storing our corporate data in our products. We do so knowing that our platform is built upon industry-standard security technology, refined principles and practices, and ongoing investments in security training, testing, independent audits, expert consulting, and advanced tooling.
Security Environment and Principles
We have a dedicated Security department consisting of over a dozen security professionals focusing on product security, security operations, incident response, risk management, and compliance. The Security Team is overseen by a Chief Information Security Officer (CISO). Our multi-layered security environment follows the principles of least privilege, separation of duties, defense in depth, and usability. Customers have ownership of user access controls and manage the entire customer data life cycle in deciding:
- What data goes into their system
- How long it should be retained
- What data should be deleted
- Who can access the data
Incident Management
We have a robust Incident Response Plan to promptly and effectively manage incidents that impact the system environment. This plan is in place to both minimize potential damages that could result from a data breach and to ensure that parties affected by the data breach are properly informed and educated on how to protect themselves.
The Security Incident Response Team (SIRT) is responsible for responding, managing, and conducting security investigations, including all aspects of communication such as deciding how, when, and to whom the findings shall be reported.
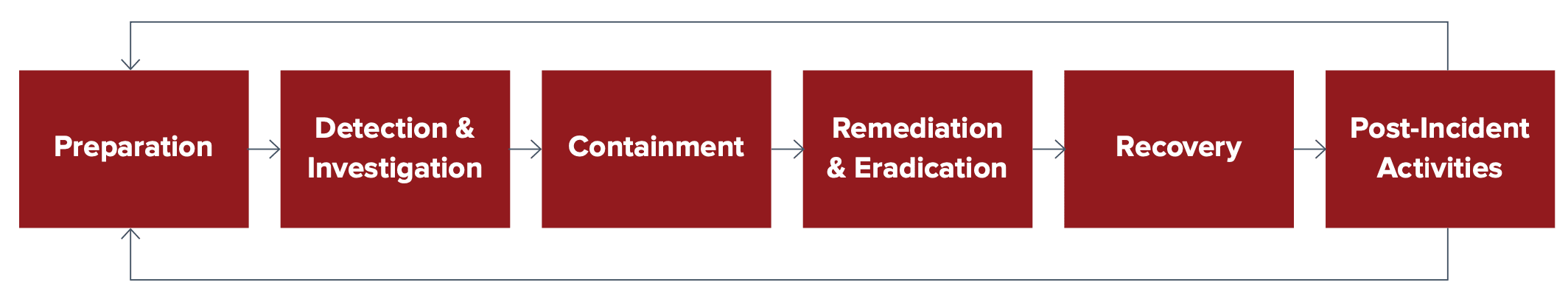
The lifecycle of a security incident at Diligent
The Diligent incident management lifecycle encompasses six phases: preparation, detection and investigation, containment, remediation and eradication, recovery, and post-incident activities.
Highbond Security Controls
Diligent Boards Security Controls