Modern Governance
Diligent Boards is part of a suite of tools that can be used to form a Modern Governance strategy. Modern governance solutions bring together historically disparate tools into one secure product suite. Board materials, voting and resolutions, evaluations, collaboration tools, document sharing, committee intelligence, candidate search, entity management – all these tools and features work together to enable seamless management and reporting.Shared Responsibility Model
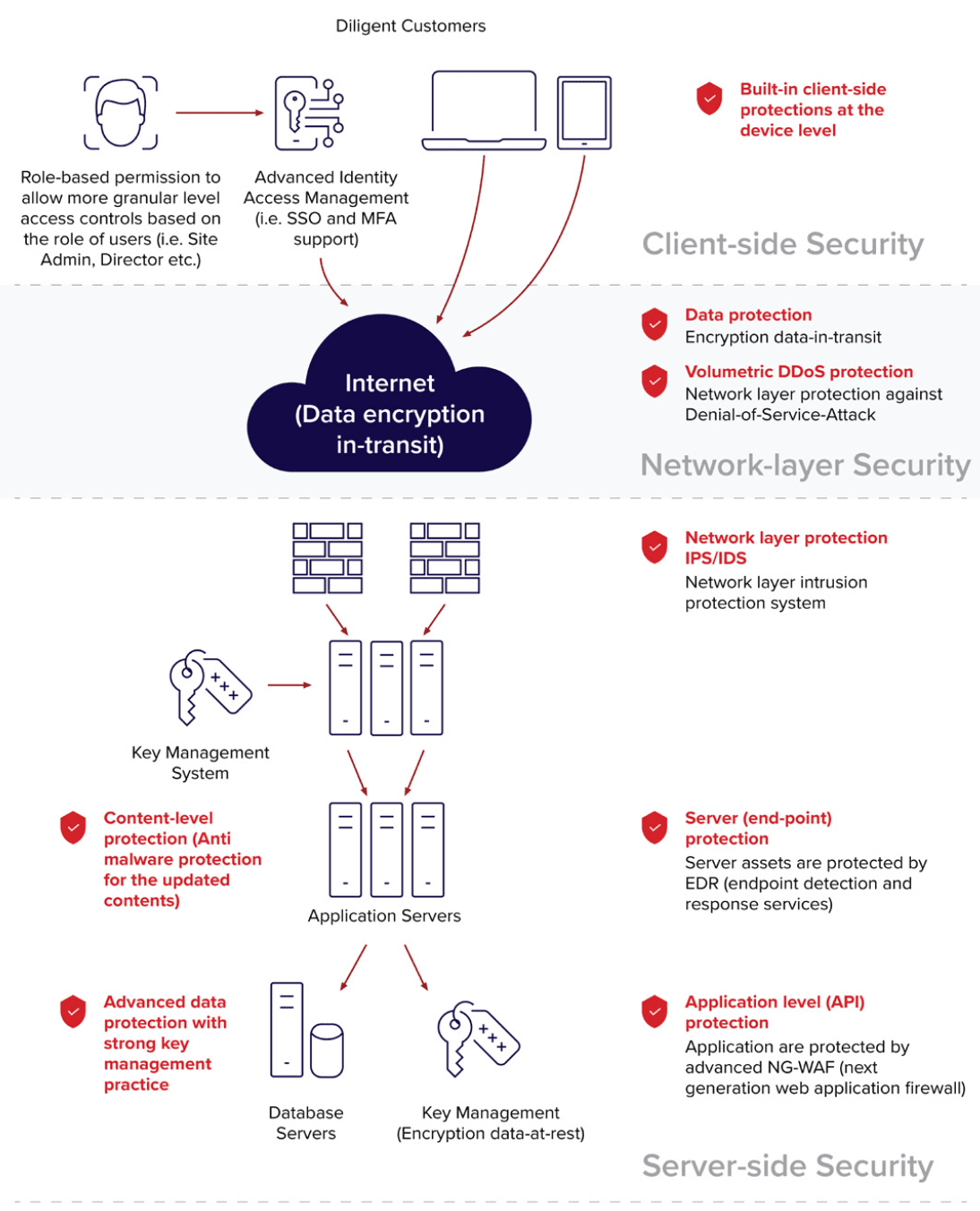
Customers share the responsibility of not only keeping their data secure, but also complying with applicable regulatory or privacy laws. Our customers have ownership of their user access controls and manage their entire data lifecycle from deciding what data goes into the system, how long it should be retained, what data should be deleted, and whom can access the data.Customer Responsibility
Customers share the responsibility of not only keeping their data secure, but also complying with applicable regulatory or privacy laws. Our customers have ownership of their user access controls and manage their entire data lifecycle from deciding what data goes into the system, how long it should be retained, what data should be deleted, and whom can access the data.Diligent Responsibility
Diligent is responsible for the physical facility as well as the physical infrastructure of server hardware, networking, and related services for the service and hosting customer data.
In addition to the physical security and infrastructure, we also have a robust information security environment to ensure that the confidentiality, integrity, and availability of customer data meets our high standards and our customers’ high expectations.
Data Encryption
We provide strong encryption of all data in transit andat rest. Encryption in transit is achieved via the industry- standard TLS (Transport Layer Security) 1.2 protocol. Public Key Infrastructure (PKI) utilizes 2048-bit RSA Public/ Private key pairs and SHA-2 for hashing.
Encryption at rest is achieved using AES utilizing Cipher Block Chaining (CBC) with a key length of 256 bits and a random initialization vector (IV). Data protection keys are managed on a per-customer basis at a minimum, with a two-key system and document-level encryption. The master encryption key is never stored in plain text and use of the customer master key to decrypt data protection keys is restricted to a Key Management Service (KMS) using a FIPS 140-2 L3 Hardware Security Module. Secrets are managed using industry-standard HSM devices.
Any data downloaded to a user’s device is encrypted by the app using an offline data protection key. This encrypts the data with AES encryption. This is in addition to any encryption provided by the device’s OS.
Identity and Access Management: Authentication
Authentication is performed by an authentication service that stores the passwords in hashed form only. Username and password are required by default and the password policy is configurable by the customer. After a set number of incorrect login attempts, user accounts are locked out of the system.Identity and Access Management: SSO / Federated Identity
The Diligent Boards Web App and iOS App support login using client identity providers. This allows customers to sign into Boards with their own identity provider, as long as it uses a supported protocol.
Currently ADFS, Azure AD, and Okta are supported via SAML 2.0. Customer can leverage federated integration to support their own SSO (single sign on) or other strong authentication methods such as adaptive or 2FA authentications based on customer’s internal security policy.
Identity and Access Management: Multifactor Authentication (MFA)
Boards users can be configured to require MFA for authentication. The second factor is dependent on the application’s platform. When accessing the web client, the user will require an SMS code, while accessing the mobile apps will require a certificate to be installed on the device. This certificate is implemented via the Device Authorization feature.Device Authorization
Device Authorization provides a 2FA solution that is compatible with the offline functionality offered by the Boards mobile applications. This feature associates a user with a specific device via a certificate installed on the device, and restricts the user’s access to Diligent Boards from that specific device. By restricting access to specific devices, customer organizations can prevent access from unknown and untrusted devices providing additional control of access rights and access locations. Device level authorization controls are also available, please contact Diligent CSM for details.Authorization
Authorization in the Diligent platform is by determined the client and set by our customer success teams. This process applies to both direct and federated identity authentication to the application.
Diligent Boards employs a role-based access control (RBAC) model. The role-based permissions in Diligent Boards support both standardized roles and granular permissions per user. Privileges such as exporting materials can be disabled.
Session Expiry
User Inactivity Timeout – Closes all windows and logs user out after specified amount of time.
- Inactive Session Timeout – Timeout period after last server request. Requires re-authentication to resume access.
- Maximum Server Session Duration – Forces reauthentication periodically according to a specified timeframe.
Platform Specific Considerations
On all platforms, Diligent Boards is designed to protect itself and data in the platform using secure design techniques and the available security resources of each platform. However, there are additional considerations outside of the controls available in Diligent client apps that can further strengthen the platform’s security.Enterprise Mobility Management/Mobile Device Management
IP restrictions allows organizations to configure one or more IP (Internet Protocol) addresses or IP address ranges from which a user may access the organization. IP restrictions may be used as an additional factor in multi-factor authentication, in addition to password credentials, to ensure only authorized users access the organization.
Diligent Boards can be configured to disable certain features. While the Diligent Boards mobile apps contains some features typically included in EMM/MDM software, implementing an actual MDM solution to enforce a security policy for the device adds another layer of control especially for email, social networking, and printing. Customers cannot distribute the iOS app from a private enterprise app store.
Device Passcodes
Requiring the use of a passcode, and preferably a strong passcode, is a first line defense in mitigating stolen devices or devices that may be accessed by unauthorized individuals.Apple Devices
Apple allows users to track, find, and wipe their missing Apple devices when Find My iPhone is turned on.Diligent Boards Web Client
The web interface code is written in industry-standard programming languages and supported by top-tier web services and web hosting. Most modern standards- compliant browsers are supported.
The following controls protect the web client:
- Boards Web is developed in accordance with Diligent’s Software Development Lifecycle (SDLC). The program adheres to secure coding practices and guidance from OWASP SAMM (Software Assurance Maturity Model).
- Development follow guidance from OWASP to code protections against the OWASP top 10 most critical web application security risks, which includes attacks such as Cross-Site Scripting (XSS) and SQL Injection.
- No plug-ins or ActiveX Controls are needed in the web browser.
- Session information is stored as short-lived bearer tokens. The access token is randomly generated and hashed.
- Boards Web has configurable inactivity timeouts and a maximum session timeout. The timeouts fully terminate the session. Boards Web communicates securely with the Boards platform using HTTPS via TLS 1.2.
- Boards Web utilizes a third-party Runtime Application Self-Protection (RASP) product. The product protects against reverse engineering, IP theft, and tamping threats.
- Diligent regularly involves a specialist third-party to perform manual application penetration testing for Boards Web, including against the OWASP Top 10.
Diligent Boards for iOS
Code Obfuscation
This security strategy intentionally complicates the code base in order to prevent reverse engineering or other compromises to the underlying structure of Diligent Boards for iOS. By protecting the underlying programming language of Diligent Boards for iOS, code obfuscation acts as an additional defense against outsiders maliciously uncovering the methodology behind our security, encryption and data transfer practices.
Jailbreak Protection
The iOS App contains jailbreak detection code that will prevent the Diligent Boards App from running on devices that have been jailbroken. A number of jailbreak detection techniques are used ranging from process forking to detection of certain files and modules that are not normally present within iOS.
Touch ID/Face ID
If enabled, Diligent Boards utilizes Apple’s proprietary fingerprint-reading technology “Touch ID” to allow users to sign in. Face ID replaces Touch ID thumbprint identification functionality on most iPhone devices, as these devices no longer have a home button or fingerprint reader. Face ID is currently present on iPhone and iPad Pro devices.
App Transitions
Screen Security prevents Diligent Boards previews from appearing in the app switcher.
Data Backup Protection
Diligent Products contain controls to ensure that application data is not backed up to iTunes or iCloud.
Logging
The Diligent Platform includes a security-auditing framework that is designed to record any changes that are made to security settings, or information that could affect security. Auditing is automatically enabled for all clients, and the audit database is available for the duration of the customer’s relationship with Diligent. All administrative functions are logged.Monitoring
Diligent uses a security information and event management (SIEM) system to provide a data analysis function that enhances the ability to detect and respond to security incidents in a timely manner. The SIEM ingests logs from applications, servers, and other infrastructure components that form the Boards production environments, acting as a central repository of aggregated logs, allowing Diligent to monitor all system access, VPN access, privilege escalation (successful and failed attempts), and end-point protection, etc. The SIEM is managed by Diligent’s Security Operations team using alerts and dashboards. Only Diligent has access to SIEM logs. Customer related application logs must be manually requested and are provided in CSV format. There is no functionality to export customer application logs into the customer’ SIEM.Alerting
Role Change Notification
If an email address is nominated by an Authorized Representative, all notification emails associated with user role changes will be sent to this address.
Account Change Notification
If an email address is nominated by an Authorized Representative, all notification emails associated with user email, security question, and password updates, will be sent to this address.
Account Lockout Notification
If an email address is nominated by an Authorized Representative, all notifications relating to a user account lockout will be sent to this address.